New 2020 CCIE/CCNP 350-701 SCOR exam questions from PassLeader 350-701 dumps! Welcome to download the newest PassLeader 350-701 VCE and PDF dumps: https://www.passleader.com/350-701.html (284 Q&As –> 311 Q&As –> 337 Q&As –> 368 Q&As –> 400 Q&As –> 429 Q&As –> 506 Q&As –> 537 Q&As –> 660 Q&As)
P.S. Free 2020 CCIE/CCNP 350-701 SCOR dumps are available on Google Drive shared by PassLeader: https://drive.google.com/open?id=1hkvcWfx1vI0RBtKa9NEv1NysJf5D2QaJ
NEW QUESTION 253
In which two ways does Easy Connect help control network access when used with Cisco TrustSec? (Choose two.)
A. It allows multiple security products to share information and work together to enhance security posture in the network.
B. It creates a dashboard in Cisco ISE that provides full visibility of all connected endpoints.
C. It allows for the assignment of Security Group Tags and does not require 802.1x to be configured on the switch or the endpoint.
D. It integrates with third-party products to provide better visibility throughout the network.
E. It allows for managed endpoints that authenticate to AD to be mapped to Security Groups (PassiveID).
Answer: CE
Explanation:
Easy Connect simplifies network access control and segmentation by allowing the assignment of Security Group Tags to endpoints without requiring 802.1X on those endpoints, whether using wired or wireless connectivity.
https://www.cisco.com/c/dam/en/us/solutions/collateral/enterprise-networks/trustsec/trustsecwith-easy-connect-configuration-guide.pdf
NEW QUESTION 254
What is the benefit of installing Cisco AMP for Endpoints on a network?
A. It provides operating system patches on the endpoints for security.
B. It provides flow-based visibility for the endpoints network connections.
C. It enables behavioral analysis to be used for the endpoints.
D. It protects endpoint systems through application control and real-time scanning.
Answer: D
NEW QUESTION 255
An administrator is configuring a DHCP server to better secure their environment. They need to be able to rate-limit the traffic and ensure that legitimate requests are not dropped. How would this be accomplished?
A. Set a trusted interface for the DHCP server.
B. Set the DHCP snooping bit to 1.
C. Add entries in the DHCP snooping database.
D. Enable ARP inspection for the required VLAN.
Answer: A
NEW QUESTION 256
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users, data, and applications. There is a requirement to use the Cisco cloud native CASB and cloud cybersecurity platform. What should be used to meet these requirements?
A. Cisco Umbrella
B. Cisco Cloud Email Security
C. Cisco NGFW
D. Cisco Cloudlock
Answer: D
Explanation:
Cisco Cloudlock: Secure your cloud users, data, and applications with the cloud-native Cloud Access Security Broker (CASB) and cloud cybersecurity platform.
https://www.cisco.com/c/dam/en/us/products/collateral/security/cloud-web-security/at-a-glancec45-738565.pdf
NEW QUESTION 257
Why is it important to implement MFA inside of an organization?
A. To prevent man-the-middle attacks from being successful.
B. To prevent DoS attacks from being successful.
C. To prevent brute force attacks from being successful.
D. To prevent phishing attacks from being successful.
Answer: C
NEW QUESTION 258
A network administrator is configuring SNMPv3 on a new router. The users have already been created; however, an additional configuration is needed to facilitate access to the SNMP views. What must the administrator do to accomplish this?
A. map SNMPv3 users to SNMP views
B. set the password to be used for SNMPv3 authentication
C. define the encryption algorithm to be used by SNMPv3
D. specify the UDP port used by SNMP
Answer: B
NEW QUESTION 259
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally manage cloud policies across these platforms. Which software should be used to accomplish this goal?
A. Cisco Defense Orchestrator
B. Cisco Secureworks
C. Cisco DNA Center
D. Cisco Configuration Professional
Answer: C
NEW QUESTION 260
How does Cisco Stealthwatch Cloud provide security for cloud environments?
A. It delivers visibility and threat detection.
B. It prevents exfiltration of sensitive data.
C. It assigns Internet-based DNS protection for clients and servers.
D. It facilitates secure connectivity between public and private networks.
Answer: A
NEW QUESTION 261
Which attack is preventable by Cisco ESA but not by the Cisco WSA?
A. buffer overflow
B. DoS
C. SQL injection
D. phishing
Answer: D
Explanation:
https://www.cisco.com/c/en/us/td/docs/security/esa/esa13-5/user_guide/b_ESA_Admin_Guide_13-5/m_advanced_phishing_protection.html
NEW QUESTION 262
A Cisco ESA administrator has been tasked with configuring the Cisco ESA to ensure there are no viruses before quarantined emails are delivered. In addition, delivery of mail from known bad mail servers must be prevented. Which two actions must be taken in order to meet these requirements? (Choose two.)
A. Use outbreak filters from SenderBase.
B. Enable a message tracking service.
C. Configure a recipient access table.
D. Deploy the Cisco ESA in the DMZ.
E. Scan quarantined emails using AntiVirus signatures.
Answer: AE
Explanation:
We should scan emails using AntiVirus signatures to make sure there are no viruses attached in emails. Note: A virus signature is the fingerprint of a virus. It is a set of unique data, or bits of code, that allow it to be identified. Antivirus software uses a virus signature to find a virus in a computer file system, allowing to detect, quarantine, and remove the virus. SenderBase is an email reputation service designed to help email administrators research senders, identify legitimate sources of email, and block spammers. When the Cisco ESA receives messages from known or highly reputable senders, it delivers them directly to the end user without any content scanning. However, when the Cisco ESA receives email messages from unknown or less reputable senders, it performs antispam and antivirus scanning.
https://www.cisco.com/c/en/us/td/docs/security/esa/esa12-0/user_guide/b_ESA_Admin_Guide_12_0/b_ESA_Admin_Guide_12_0_chapter_0100100.html
NEW QUESTION 263
Which type of dashboard does Cisco DNA Center provide for complete control of the network?
A. service management
B. centralized management
C. application management
D. distributed management
Answer: B
Explanation:
Cisco’s DNA Center is the only centralized network management system to bring all of this functionality into a single pane of glass.
https://www.cisco.com/c/en/us/products/collateral/cloud-systems-management/dna-center/nb-06-dna-center-faq-cte-en.html
NEW QUESTION 264
In an IaaS cloud services model, which security function is the provider responsible for managing?
A. Internet proxy
B. firewalling virtual machines
C. CASB
D. hypervisor OS hardening
Answer: D
Explanation:
Infrastructure as a Service (IaaS) in cloud computing is one of the most significant and fastest growing field. In this service model, cloud providers offer resources to users/machines that include computers as virtual machines, raw (block) storage, firewalls, load balancers, and network devices.
NEW QUESTION 265
A network engineer has been tasked with adding a new medical device to the network. Cisco ISE is being used as the NAC server, and the new device does not have a supplicant available. What must be done in order to securely connect this device to the network?
A. Use MAB with profiling.
B. Use MAB with posture assessment.
C. Use 802.1X with posture assessment.
D. Use 802.1X with profiling.
Answer: A
Explanation:
As the new device does not have a supplicant, we cannot use 802.1X. MAC Authentication Bypass (MAB) is a fallback option for devices that don’t support 802.1X. It is virtually always used in deployments in some way shape or form. MAB works by having the authenticator take the connecting device’s MAC address and send it to the authentication server as its username and password. The authentication server will check its policies and send back an Access-Accept or Access-Reject just like it would with 802.1X. Cisco ISE Profiling Services provides dynamic detection and classification of endpoints connected to the network. Using MAC addresses as the unique identifier, ISE collects various attributes for each network endpoint to build an internal endpoint database. The classification process matches the collected attributes to prebuilt or user-defined conditions, which are then correlated to an extensive library of profiles. These profiles include a wide range of device types, including mobile clients (iPads, Android tablets, Chromebooks, and so on), desktop operating systems (for example, Windows, Mac OS X, Linux, and others), and numerous non-user systems such as printers, phones, cameras, and game consoles. Once classified, endpoints can be authorized to the network and granted access based on their profile. For example, endpoints that match the IP phone profile can be placed into a voice VLAN using MAC Authentication Bypass (MAB) as the authentication method. Another example is to provide differentiated network access to users based on the device used. For example, employees can get full access when accessing the network from their corporate workstation but be granted limited network access when accessing the network from their personal iPhone.
https://community.cisco.com/t5/security-documents/ise-profiling-design-guide/ta-p/3739456
NEW QUESTION 266
An organization has noticed an increase in malicious content downloads and wants to use Cisco Umbrella to prevent this activity for suspicious domains while allowing normal web traffic. Which action will accomplish this task?
A. Set content settings to High.
B. Configure the intelligent proxy.
C. Use destination block lists.
D. Configure application block lists.
Answer: B
Explanation:
Obviously, if you allow all traffic to these risky domains, users might access malicious content, resulting in an infection or data leak. But if you block traffic, you can expect false positives, an increase in support inquiries, and thus, more headaches. By only proxying risky domains, the intelligent proxy delivers more granular visibility and control. The intelligent proxy bridges the gap by allowing access to most known good sites without being proxied and only proxying those that pose a potential risk. The proxy then filters and blocks against specific URLs hosting malware while allowing access to everything else.
https://docs.umbrella.com/deployment-umbrella/docs/what-is-the-intelligent-proxy
NEW QUESTION 267
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior of users?
A. file access from a different user
B. interesting file access
C. user login suspicious behavior
D. privilege escalation
Answer: C
Explanation:
https://www.cisco.com/c/en/us/products/collateral/data-center-analytics/tetration-analytics/whitepaper-c11-740380.html
NEW QUESTION 268
A network administrator is configuring a switch to use Cisco ISE for 802.1X. An endpoint is failing authentication and is unable to access the network. Where should the administrator begin troubleshooting to verify the authentication details?
A. Adaptive Network Control Policy List
B. Context Visibility
C. Accounting Reports
D. RADIUS Live Logs
Answer: D
Explanation:
https://community.cisco.com/t5/security-documents/how-to-troubleshoot-ise-failedauthentications-amp/ta-p/3630960
NEW QUESTION 269
Which method is used to deploy certificates and configure the supplicant on mobile devices to gain access to network resources?
A. BYOD on boarding.
B. Simple Certificate Enrollment Protocol.
C. Client provisioning.
D. MAC authentication bypass.
Answer: A
Explanation:
When supporting personal devices on a corporate network, you must protect network services and enterprise data by authenticating and authorizing users (employees, contractors, and guests) and their devices. Cisco ISE provides the tools you need to allow employees to securely use personal devices on a corporate network. Guests can add their personal devices to the network by running the native supplicant provisioning (Network Setup Assistant), or by adding their devices to the My Devices portal. Because native supplicant profiles are not available for all devices, users can use the My Devices portal to add these devices manually; or you can configure Bring Your Own Device (BYOD) rules to register these devices.
https://www.cisco.com/c/en/us/td/docs/security/ise/2-4/admin_guide/b_ISE_admin_guide_24/m_ise_devices_byod.html
NEW QUESTION 270
An organization is trying to implement micro-segmentation on the network and wants to be able to gain visibility on the applications within the network. The solution must be able to maintain and force compliance. Which product should be used to meet these requirements?
A. Cisco Umbrella
B. Cisco AMP
C. Cisco Stealthwatch
D. Cisco Tetration
Answer: D
Explanation:
Micro-segmentation secures applications by expressly allowing particular application traffic and, by default, denying all other traffic. Micro-segmentation is the foundation for implementing a zero-trust security model for application workloads in the data center and cloud. Cisco Tetration is an application workload security platform designed to secure your compute instances across any infrastructure and any cloud. To achieve this, it uses behavior and attribute-driven microsegmentation policy generation and enforcement. It enables trusted access through automated, exhaustive context from various systems to automatically adapt security policies. To generate accurate microsegmentation policy, Cisco Tetration performs application dependency mapping to discover the relationships between different application tiers and infrastructure services. In addition, the platform supports “what-if” policy analysis using real-time data or historical data to assist in the validation and risk assessment of policy application pre-enforcement to ensure ongoing application availability. The normalized microsegmentation policy can be enforced through the application workload itself for a consistent approach to workload microsegmentation across any environment, including virtualized, bare-metal, and container workloads running in any public cloud or any data center. Once the microsegmentation policy is enforced, Cisco Tetration continues to monitor for compliance deviations, ensuring the segmentation policy is up to date as the application behavior change.
https://www.cisco.com/c/en/us/products/collateral/data-center-analytics/tetration-analytics/solution-overview-c22-739268.pdf
NEW QUESTION 271
Which term describes when the Cisco Firepower downloads threat intelligence updates from Cisco Talos?
A. consumption
B. sharing
C. analysis
D. authoring
Answer: A
Explanation:
https://blogs.cisco.com/developer/automate-threat-intelligence-using-cisco-threat-intelligencedirector
NEW QUESTION 272
What are two characteristics of Cisco DNA Center APIs? (Choose two.)
A. Postman is required to utilize Cisco DNA Center API calls.
B. They do not support Python scripts.
C. They are Cisco proprietary.
D. They quickly provision new devices.
E. They view the overall health of the network.
Answer: DE
NEW QUESTION 273
What is a benefit of conducting device compliance checks?
A. It indicates what type of operating system is connecting to the network.
B. It validates if anti-virus software is installed.
C. It scans endpoints to determine if malicious activity is taking place.
D. It detects email phishing attacks.
Answer: B
NEW QUESTION 274
Drag and Drop
Drag and drop the NetFlow export formats from the left onto the descriptions on the right.
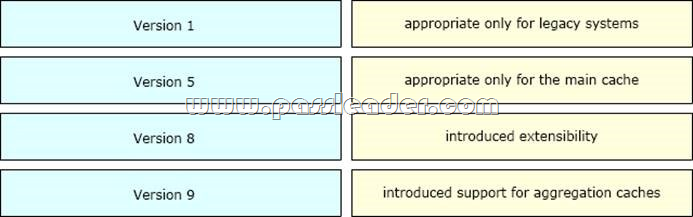
Answer:

Explanation:
The Version 1 format was the initially released version. Do not use the Version 1 format unless you are using a legacy collection system that requires it. Use Version 9 or Version 5 export format. Version 5 export format is suitable only for the main cache; it cannot be expanded to support new features. Version 8 export format is available only for aggregation caches; it cannot be expanded to support new features.
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/netflow/configuration/15-mt/nf-15-mtbook/cfg-nflow-data-expt.html
NEW QUESTION 275
Drag and Drop
Drag and drop the solutions from the left onto the solution’s benefits on the right.
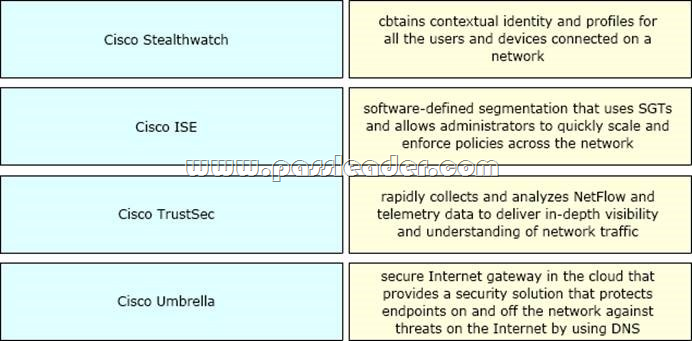
NEW QUESTION 276
……
New 2020 CCIE/CCNP 350-701 SCOR exam questions from PassLeader 350-701 dumps! Welcome to download the newest PassLeader 350-701 VCE and PDF dumps: https://www.passleader.com/350-701.html (284 Q&As –> 311 Q&As –> 337 Q&As –> 368 Q&As –> 400 Q&As –> 429 Q&As –> 506 Q&As –> 537 Q&As –> 660 Q&As)
P.S. Free 2020 CCIE/CCNP 350-701 SCOR dumps are available on Google Drive shared by PassLeader: https://drive.google.com/open?id=1hkvcWfx1vI0RBtKa9NEv1NysJf5D2QaJ






