New 2020 CyberOps 300-215 CBRFIR exam questions from PassLeader 300-215 dumps! Welcome to download the newest PassLeader 300-215 VCE and PDF dumps: https://www.passleader.com/300-215.html (65 Q&As)
P.S. Free 2020 CyberOps 300-215 CBRFIR dumps are available on Google Drive shared by PassLeader: https://drive.google.com/drive/folders/1nyKDimd8mnTLP0fZ2oIasK0jvcxsBzE0
NEW QUESTION 1
An investigator is analyzing an attack in which malicious files were loaded on the network and were undetected. Several of the images received during the attack include repetitive patterns. Which anti-forensic technique was used?
A. spoofing
B. obfuscation
C. tunneling
D. steganography
Answer: D
Explanation:
https://doi.org/10.5120/1398-1887 https://www.carbonblack.com/blog/steganography-in-the-modern-attack-landscape/
NEW QUESTION 2
Which tool conducts memory analysis?
A. MemDump
B. Sysinternals Autoruns
C. Volatility
D. Memoryze
Answer: C
Explanation:
https://resources.infosecinstitute.com/topic/memory-forensics-and-analysis-using-volatility/
NEW QUESTION 3
What is the goal of an incident response plan?
A. to identify critical systems and resources in an organization
B. to ensure systems are in place to prevent an attack
C. to determine security weaknesses and recommend solutions
D. to contain an attack and prevent it from spreading
Answer: D
Explanation:
https://www.forcepoint.com/cyber-edu/incident-response
NEW QUESTION 4
An attacker embedded a macro within a word processing file opened by a user in an organization’s legal department. The attacker used this technique to gain access to confidential financial data. Which two recommendations should a security expert make to mitigate this type of attack? (Choose two.)
A. controlled folder access
B. removable device restrictions
C. signed macro requirements
D. firewall rules creation
E. network access control
Answer: AC
NEW QUESTION 5
What is a use of TCPdump?
A. to analyze IP and other packets
B. to view encrypted data fields
C. to decode user credentials
D. to change IP ports
Answer: A
Explanation:
https://en.wikipedia.org/wiki/Tcpdump
NEW QUESTION 6
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
A. process injection
B. privilege escalation
C. GPO modification
D. token manipulation
Answer: A
Explanation:
https://attack.mitre.org/techniques/T1055/
NEW QUESTION 7
Which tool is used for reverse engineering malware?
A. Ghidra
B. SNORT
C. Wireshark
D. NMAP
Answer: A
Explanation:
https://www.nsa.gov/resources/everyone/ghidra/#:~:text=Ghidra%20is%20a%20software%20reverse,in%20their%20networks%20and%20systems
NEW QUESTION 8
What are YARA rules based upon?
A. binary patterns
B. HTML code
C. network artifacts
D. IP addresses
Answer: A
Explanation:
https://en.wikipedia.org/wiki/YARA#:~:text=YARA%20is%20the%20name%20of,strings%20and%20a%20boolean%20expression
NEW QUESTION 9
A security team received reports of users receiving emails linked to external or unknown URLs that are non-returnable and non-deliverable. The ISP also reported a 500% increase in the amount of ingress and egress email traffic received. After detecting the problem, the security team moves to the recovery phase in their incident response plan. Which two actions should be taken in the recovery phase of this incident? (Choose two.)
A. verify the breadth of the attack
B. collect logs
C. request packet capture
D. remove vulnerabilities
E. scan hosts with updated signatures
Answer: DE
NEW QUESTION 10
An organization recovered from a recent ransomware outbreak that resulted in significant business damage. Leadership requested a report that identifies the problems that triggered the incident and the security team’s approach to address these problems to prevent a reoccurrence. Which components of the incident should an engineer analyze first for this report?
A. impact and flow
B. cause and effect
C. risk and RPN
D. motive and factors
Answer: D
NEW QUESTION 11
Drag and Drop
Drag and drop the cloud characteristic from the left onto the challenges presented for gathering evidence on the right.
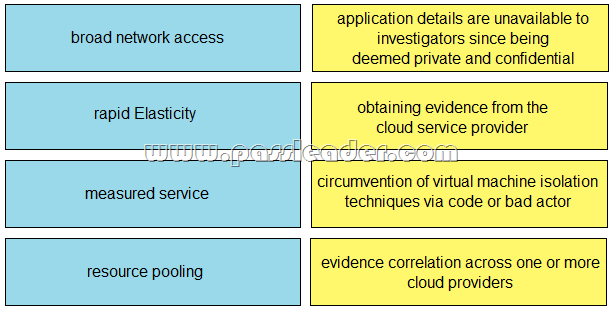
NEW QUESTION 12
Drag and Drop
Drag and drop the steps from the left into the order to perform forensics analysis of infrastructure networks on the right.

Answer:

Explanation:
https://subscription.packtpub.com/book/networking_and_servers/9781789344523/1/ch01lvl1sec12/network-forensics-investigation-methodology
NEW QUESTION 13
……
New 2020 CyberOps 300-215 CBRFIR exam questions from PassLeader 300-215 dumps! Welcome to download the newest PassLeader 300-215 VCE and PDF dumps: https://www.passleader.com/300-215.html (65 Q&As)
P.S. Free 2020 CyberOps 300-215 CBRFIR dumps are available on Google Drive shared by PassLeader: https://drive.google.com/drive/folders/1nyKDimd8mnTLP0fZ2oIasK0jvcxsBzE0






