New 350-018 exam questions from PassLeader 350-018 dumps! Welcome to download the newest PassLeader 350-018 VCE and PDF dumps: http://www.passleader.com/350-018.html (894 Q&As)
P.S. Free 350-018 dumps are available on Google Drive shared by PassLeader: https://drive.google.com/open?id=0B-ob6L_QjGLpfjE1cHRyNEtmX3JfdU9CUFlRZnVxNjZUbWxsSnBpNXM0QjZYZjBXZVgyOTQ
QUESTION 91
Which three statements about IKEv2 are correct? (Choose three.)
A. INITIAL_CONTACT is used to synchronize state between peers.
B. The IKEv2 standard defines a method for fragmenting large messages.
C. The initial exchanges of IKEv2 consist of IKE_SA_INIT and IKE_AUTH.
D. Rekeying IKE and child SAs is facilitated by the IKEv2 CREATE_CHILD_SA exchange.
E. NAT-T is not supported.
F. Attribute policy push (via the configuration payload) is only supported in REQUEST/REPLY mode.
Answer: ACD
QUESTION 92
Which three statements about LDAP are true? (Choose three.)
A. LDAP uses UDP port 389 by default.
B. LDAP is defined in terms of ASN.1 and transmitted using BER.
C. LDAP is used for accessing X.500 directory services.
D. An LDAP directory entry is uniquely identified by its DN.
E. A secure connection via TLS is established via the UseTLS operation.
Answer: BCD
QUESTION 93
Which two EAP methods may be susceptible to offline dictionary attacks? (Choose two.)
A. EAP-MD5
B. LEAP
C. PEAP with MS-CHAPv2
D. EAP-FAST
Answer: AB
QUESTION 94
Which PKCS is invoked during IKE MM5 and MM6 when digital certificates are used as the authentication method?
A. PKCS#7
B. PKCS#10
C. PKCS#13
D. PKCS#11
E. PKCS#3
Answer: A
QUESTION 95
Which mode of operation must be enabled on CSM to support roles such as Network Administrator, Approver, Network Operator, and Help Desk?
A. Deployment Mode
B. Activity Mode
C. Workflow Mode
D. User Roles Mode
E. Administration Mode
F. Network Mode
Answer: C
QUESTION 96
Which two ISE Probes would be required to distinguish accurately the difference between an iPad and a MacBook Pro? (Choose two.)
A. DHCP or DHCPSPAN
B. SNMPTRAP
C. SNMPQUERY
D. NESSUS
E. HTTP
F. DHCP TRAP
Answer: AE
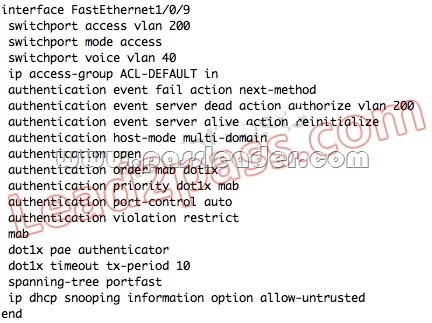
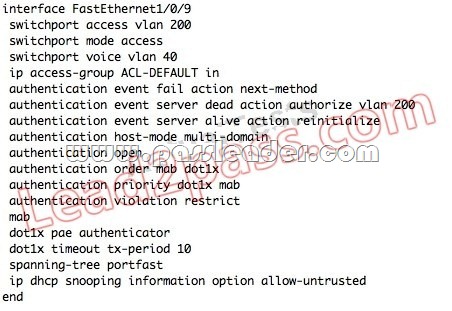
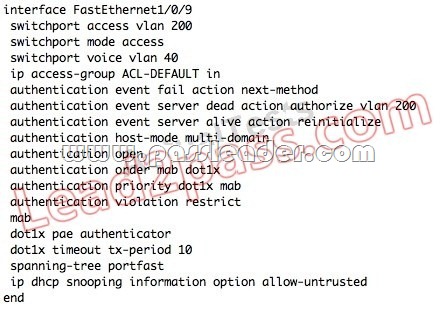
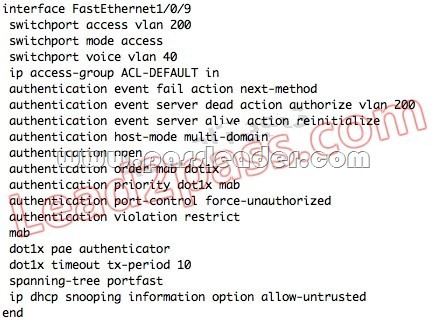
QUESTION 97
Which configuration option will correctly process network authentication and authorization using both 802.1X and MAB on a single port?
Answer: B
QUESTION 98
Which statement regarding the routing functions of the Cisco ASA is true?
A. The translation table can override the routing table for new connections.
B. The ASA supports policy-based routing with route maps.
C. In a failover pair of ASAs, the standby firewall establishes a peer relationship with OSPF neighbors.
D. Routes to the Null0 interface can be configured to black-hole traffic.
Answer: A
QUESTION 99
Which three statements are true about the Cisco ASA object configuration below? (Choose three.)
object network vpnclients
range 10.1.100.4 10.1.100.10
object network vpnclients
nat (outside,outside) dynamic interface
A. The NAT configuration in the object specifies a PAT rule.
B. This configuration requires the command same-security-traffic inter-interface for traffic that matches this NAT rule to pass through the Cisco ASA appliance.
C. The NAT rule of this object will be placed in Section 1 (Auto-NAT) of the Cisco ASA NAT table.
D. This configuration is most likely used to provide Internet access to connected VPN clients.
E. Addresses in the range will be assigned during config-mode.
Answer: ABD
Explanation:
http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-next-generation-firewalls/116388-technote-nat-00.html
QUESTION 100
Which three attributes may be configured as part of the Common Tasks panel of an authorization profile in the Cisco ISE solution? (Choose three.)
A. VLAN
B. voice VLAN
C. dACL name
D. voice domain permission
E. SGT
Answer: ACD
QUESTION 101
Which two statements describe the Cisco TrustSec system correctly? (Choose two.)
A. The Cisco TrustSec system is a partner program, where Cisco certifies third-party security products as extensions to the secure infrastructure.
B. The Cisco TrustSec system is an approach to certifying multimedia and collaboration applications as secure.
C. The Cisco TrustSec system is an Advanced Network Access Control System that leverages enforcement intelligence in the network infrastructure.
D. The Cisco TrustSec system tests and certifies all products and product versions that make up the system as working together in a validated manner.
Answer: CD
QUESTION 102
Which option is the correct definition for MAB?
A. MAB is the process of checking the mac-address-table on the local switch for the sticky address.
If the mac-address of the device attempting to access the network matches the configured sticky address, it will be permitted to bypass 802.1X authentication.
B. MAB is a process where the switch will send an authentication request on behalf of the endpoint that is attempting to access the network, using the mac-address of the device as the credentials.
The authentication server evaluates that MAC address against a list of devices permitted to access the network without a stronger authentication.
C. MAB is a process where the switch will check a local list of MAC addresses to identify systems that are permitted network access without using 802.1X.
D. MAB is a process where the supplicant on the endpoint is configured to send the MAC address of the endpoint as its credentials.
Answer: B
QUESTION 103
Which three statements are true about the Cisco NAC Appliance solution? (Choose three.)
A. In a Layer 3 OOB ACL deployment of the Cisco NAC Appliance, the discovery host must be configured as the untrusted IP address of the Cisco NAC Appliance Server.
B. In a Cisco NAC Appliance deployment, the discovery host must be configured on a Cisco router using the “NAC discovery-host” global configuration command.
C. In a VRF-style OOB deployment of the Cisco NAC Appliance, the discovery host may be the IP address that is on the trusted side of the Cisco NAC Appliance Server.
D. In a Layer 3 IB deployment of the Cisco NAC Appliance, the discovery host may be configured as the IP address of the Cisco NAC Appliance Manager.
Answer: ACD
QUESTION 104
Refer to the exhibit, which shows a partial output of the show command. Which statement best describes the problem?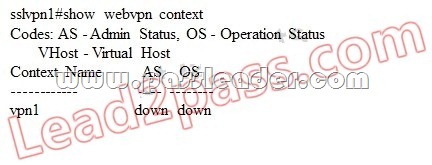
A. Context vpn1 is not inservice.
B. There is no gateway that is configured under context vpn1.
C. The config has not been properly updated for context vpn1.
D. The gateway that is configured under context vpn1 is not inservice.
Answer: A
QUESTION 105
Review the exhibit. Which three statements about the Cisco IPS sensor are true? (Choose three.)
A. A
B. B
C. C
D. D
E. E
Answer: ACE
QUESTION 106
Refer to the exhibit. Which three command sets are required to complete this IPv6 IPsec site-to-site VTI? (Choose three.)
A. interface Tunnel0
tunnel mode ipsec ipv6
B. crypto isakmp-profile
match identity address ipv6 any
C. interface Tunnel0
ipv6 enable
D. ipv6 unicast-routing
E. interface Tunnel0
ipv6 enable-ipsec
Answer: ACD
QUESTION 107
An internal DNS server requires a NAT on a Cisco IOS router that is dual-homed to separate ISPs using distinct CIDR blocks. Which NAT capability is required to allow hosts in each CIDR block to contact the DNS server via one translated address?
A. NAT overload
B. NAT extendable
C. NAT TCP load balancing
D. NAT service-type DNS
E. NAT port-to-application mapping
Answer: B
QUESTION 108
Refer to the exhibit. Which option correctly identifies the point on the exhibit where Control Plane Policing (input) is applied to incoming packets?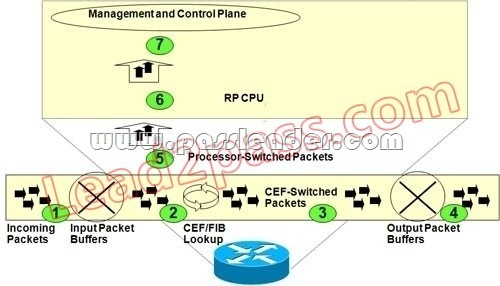
A. point 6
B. point 7
C. point 4
D. point 1
E. points 5 and 6
Answer: A
QUESTION 109
Which QoS marking is only locally significant on a Cisco router?
A. MPLS EXP
B. DSCP
C. QoS group
D. IP precedence
E. traffic class
F. flow label
Answer: C
QUESTION 110
Which three control plane subinterfaces are available when implementing Cisco IOS Control Plane Protection? (Choose three.)
A. CPU
B. host
C. fast-cache
D. transit
E. CEF-exception
F. management
Answer: BDE
QUESTION 111
Management Frame Protection is available in two deployment modes, Infrastructure and Client. Which three statements describe the differences between these modes? (Choose three.)
A. Infrastructure mode appends a MIC to management frames.
B. Client mode encrypts management frames.
C. Infrastructure mode can detect and prevent common DoS attacks.
D. Client mode can detect and prevent common DoS attacks.
E. Infrastructure mode requires Cisco Compatible Extensions version 5 support on clients.
Answer: ABD
QUESTION 112
Which three object tracking options are supported by Cisco IOS policy-based routing? (Choose three.)
A. absence of an entry in the routing table
B. existence of a CDP neighbor relationship
C. existence of an entry in the routing table
D. results of an SAA operation
E. state of the line protocol of an interface
Answer: CDE
QUESTION 113
Which four protocols are supported by Cisco IOS Management Plane Protection? (Choose four.)
A. Blocks Extensible Exchange Protocol (BEEP)
B. Hypertext Transfer Protocol Secure (HTTPS)
C. Secure Copy Protocol (SCP)
D. Secure File Transfer Protocol (SFTP)
E. Secure Shell (SSH)
F. Simple Network Management Protocol (SNMP)
Answer: ABEF
QUESTION 114
Which four Cisco IOS features are used to implement First Hop Security in IPv6? (Choose four.)
A. IPv6 First-Hop Security Binding Table
B. IPv6 Device Tracking
C. IPv6 RA Guard
D. SeND
E. IPv6 Selective Packet Discard
F. IPv6 Source Guard
Answer: ABCD
QUESTION 115
According ISO27001 ISMS, which of the following are mandatory documents? (Choose 4)
A. ISMS Policy
B. Corrective Action Procedure
C. IS Procedures
D. Risk Assessment Reports
E. Complete Inventory of all information assets
Answer: ABCD
QUESTION 116
Which current RFC made RFCs 2409, 2407, and 2408 obsolete?
A. RFC 4306
B. RFC 2401
C. RFC 5996
D. RFC 4301
E. RFC 1825
Answer: C
QUESTION 117
Which of these is a core function of the risk assessment process? (Choose one.)
A. performing regular network upgrades
B. performing network optimization
C. performing network posture validation
D. establishing network baselines
E. prioritizing network roll-outs
Answer: C
QUESTION 118
Which two answers describe provisions of the SOX Act and its international counterpart Acts? (Choose two.)
A. confidentiality and integrity of customer records and credit card information
B. accountability in the event of corporate fraud
C. financial information handled by entities such as banks, and mortgage and insurance brokers
D. assurance of the accuracy of financial records
E. US Federal government information
F. security standards that protect healthcare patient data
Answer: BD
QUESTION 119
In order to reassemble IP fragments into a complete IP datagram, which three IP header fields are referenced by the receiver? (Choose three.)
A. don’t fragment flag
B. packet is fragmented flag
C. IP identification field
D. more fragment flag
E. number of fragments field
F. fragment offset field
Answer: CDF
QUESTION 120
Which VTP mode allows the Cisco Catalyst switch administrator to make changes to the VLAN configuration that only affect the local switch and are not propagated to other switches in the VTP domain?
A. transparent
B. server
C. client
D. local
E. pass-through
Answer: A
New 350-018 exam questions from PassLeader 350-018 dumps! Welcome to download the newest PassLeader 350-018 VCE and PDF dumps: http://www.passleader.com/350-018.html (894 Q&As)
P.S. Free 350-018 dumps are available on Google Drive shared by PassLeader: https://drive.google.com/open?id=0B-ob6L_QjGLpfjE1cHRyNEtmX3JfdU9CUFlRZnVxNjZUbWxsSnBpNXM0QjZYZjBXZVgyOTQ